Some time ago I described how to install Git For Windows and how to use it in IntelliJ Idea. See here for details. I realised that from time to time I go back to those things:
- modifying git config files and trying to find them
- working with passwords
- using different editor for commit message
Let's take a closer look.
Modifying git config files and trying to find them.
Git uses three different config files (usually named .gitconfig) at three different levels:
System
Location: [your_git_for_windows_instalation_path]/etc/.gitconfig or [your_git_for_windows_instalation_path]/mingw64/etc/.gitconfig.
Purpose: contains values applied to every user on the system and all their repositories. If we want to read/write from/to this file we have to pass --system option. Because this is a system configuration file, you may need superuser privilege to make changes to it.
Global
Location: [windows_user_directory]/.gitconfig
Purpose: contains values applied to certain (usually logged in) user on the system and all repositories this user works with. If we want to read/write from/to this file we have to pass --global option.
Project
Location: [project_directory]/.gitconfig
Working with passwords.
During installation process Git For Windows offers to install Git Credential Manager (GCM) - a tool for storing passwords in a secured way.
But what if want to enter password every time when we push/pull code from remote repository? We can select "None" when Git installer asks for manager. But what if we already installed it and we want to remove it? We have to entirely remove below entry from system config file:
[credential]
helper = manager
Git will start to ask for passord every time, but it will do it using OpenSSH popup window. If we want to disable it in order to enter password directly from command line (or in terminal window in IntellJ), we have to add empty entry for system config file by executing this command:
Git will start to ask for passord every time, but it will do it using OpenSSH popup window. If we want to disable it in order to enter password directly from command line (or in terminal window in IntellJ), we have to add empty entry for system config file by executing this command:
git config --system core.askpass ""
If You really want to not to enter password every time during pull/push with remote repository it is better to use SSH keys.
Using different editor for commit message.
By default Git For Windows offers to install vim as a default editor for commit messages. It is XXI century, we have many great editors under Windows, so do not do this mistake and do not install this archaic editor for linux geeks ;) Why? Let's demonstrate it with example.
1. We have a "Hello World" java application maintained by Git:
2. When we commit changes and in the commit command we pass commit message, we will not find any issues with the vim:
3. But let's use a commit command where no commit message is passed and we expect an editor to open and let us put message there. W use git commit command without "-m" option:
As we see vim is opened in the terminal and after start insertion mode (press Insert) we can type in commit message. Now we have to save the commit message. As You know we have to press Esc in vim to exit insert mode and type something like :wq!.
Good luck :) When You press Esc focus is switched to the Main.java file instead of terminal where vim is opened. It is a known issue in IntelliJ when using Git in its terminal: https://stackoverflow.com/questions/67848200/how-do-i-commit-a-git-message-in-intellijs-terminal
In short: You have to change Esc key binding to switch focus under IntelliJ (assign different key not only remove Esc). Or if You have luck and do left-click (on some area different than file edit window) with Esc, You may sooner or later exit from insert mode:
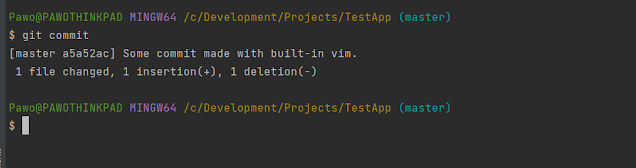
After typing :wq! we see that commit is complete with our message:
You can now say: "What a problem, just change this binding if You still want to use git from terminal. Or just use excellent graphic integration with git from IntelliJ". I would say: "Maybe it is high time use excellent external editor which I use every day instead of archaic one which I have to configure in unusual way".
4. Solution: use external editor instead of vim (here I will use Sublime).
First we define default editor in git system config file using this command:
git config --system core.editor "'C:/Dodatkowe/Sublime/subl.exe' -w"
Now we check if there are any entries about core.editor in global config file and specific project config file (which may override system setting). If we find any, remove them. Now let's try to use Sublime as editor:
After typing in git commit Sublime editor is opened in new window, where we can type in our commit message. Please notice what IntelliJ displays in terminal:
hint: Waiting for your editor to close the file...
Yes, it is wating until You save the file and close Sublime (when using vim it is also display this message, but exiting there is harder ;)). So lets save the file by Ctrl+S and close the Sublime:
It works without changing anything in IntelliJ.